Challenge
Challenge description:
We caught a threat actor, called MuddyWater, bruteforcing a login for our Domain Controller. We have a packet capture of the intrustion. Can you figure out which account they logged in to and what the password is?
Flag format is swampCTF{<username>:<password>}
Writeup also available on my blog
Filtering
We are given a .pcap file, which we can open in WireShark or other similar software.
There are 97k packets in this file, so we need to filter to find data that’s useful to us.
When we open the file and scroll, we can see lots of SMB2 packets with “Error: STATUS_LOGON_FAILURE” and “Error: STATUS_MORE_PROCESSING_REQUIRED”:
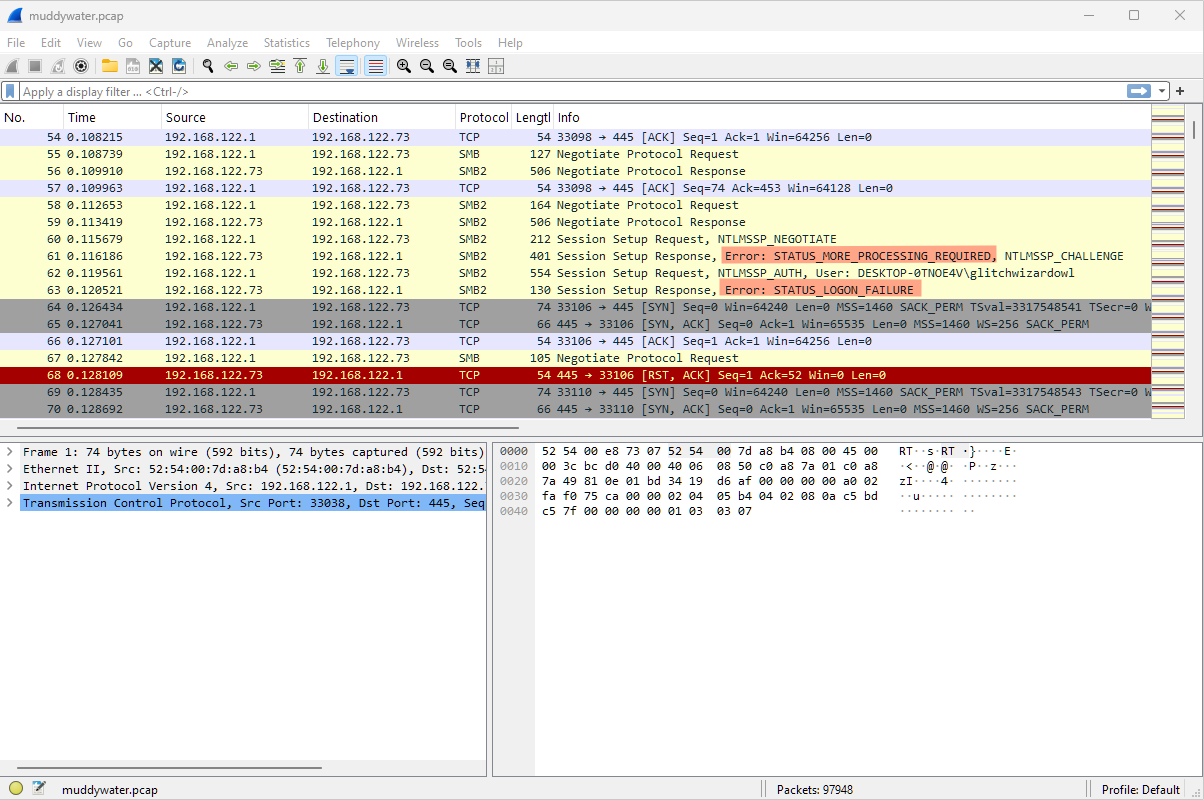
How can we filter these out?
If we click on one of them we can look at the SMB2 details:
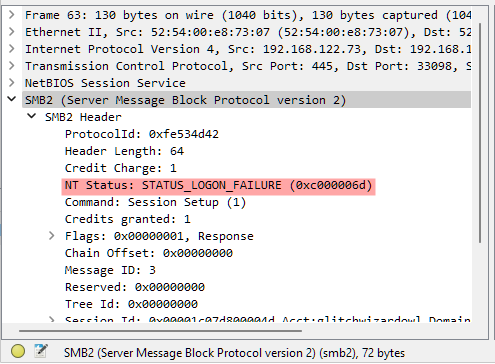
We can see that the one related to this error is NT Status, to copy the value in brackets right-click this field and choose Copy -> Value.
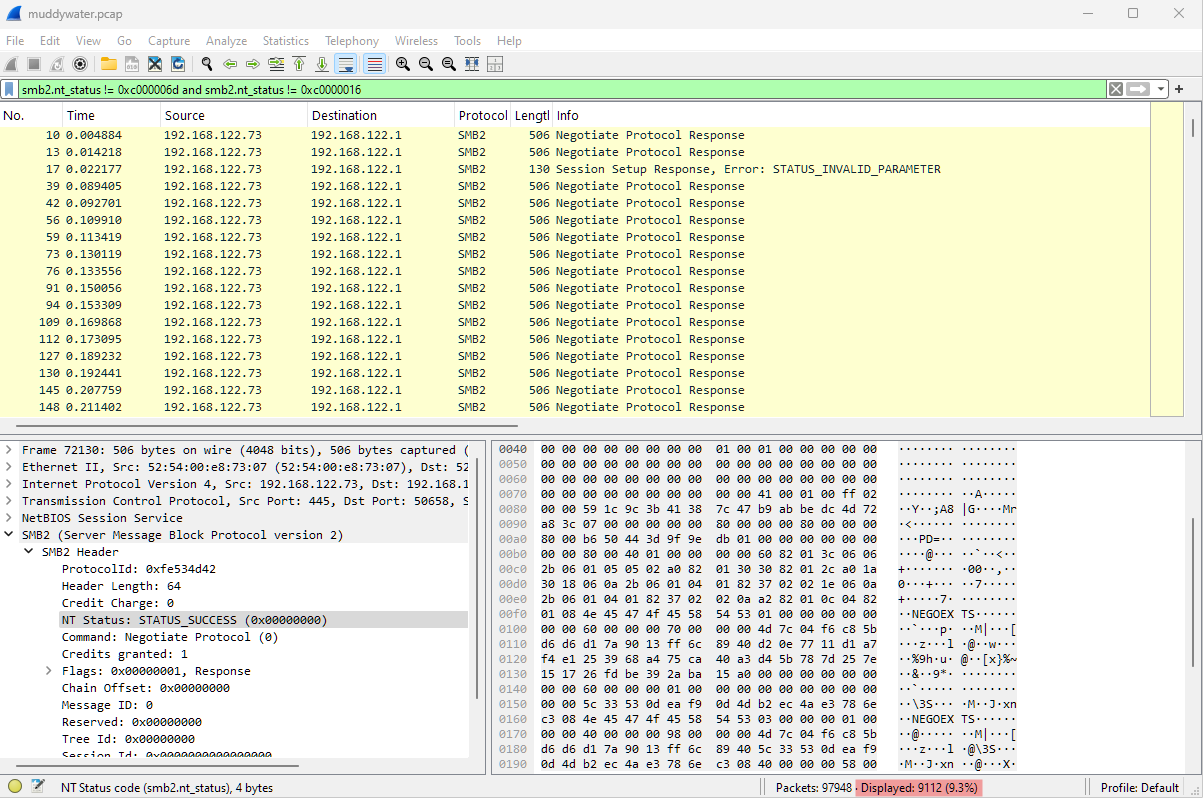
After this we can filter it out with the display filter smb2.nt_status != 0xc000006d, this still leaves all the STATUS_MORE_PROCESSING_REQURIED errors.
To filter both out we can use the display filter smb2.nt_status != 0xc000006d and smb2.nt_status != 0xc0000016, which leaves us with ~9000 packets displayed out of the 97k total packets:
There’s still lots of Negotiate Protocol Response packets in the list, let’s filter those too with and smb2.cmd != 0 which leaves us with just 3 packets:
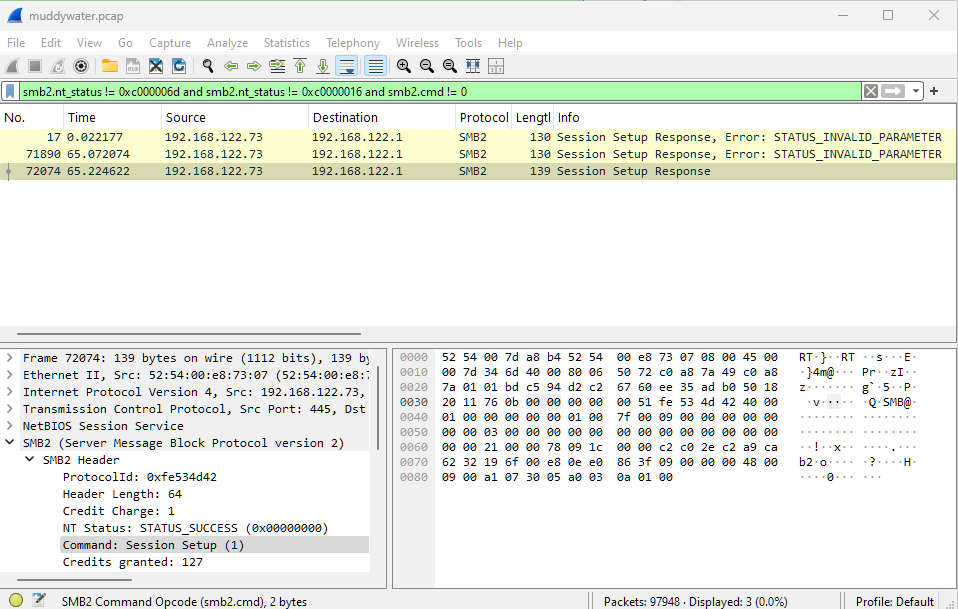
Now we can right-click packet number 72074 and choose Follow -> TCP Stream to filter to just this conversation, we can close the window that comes up.
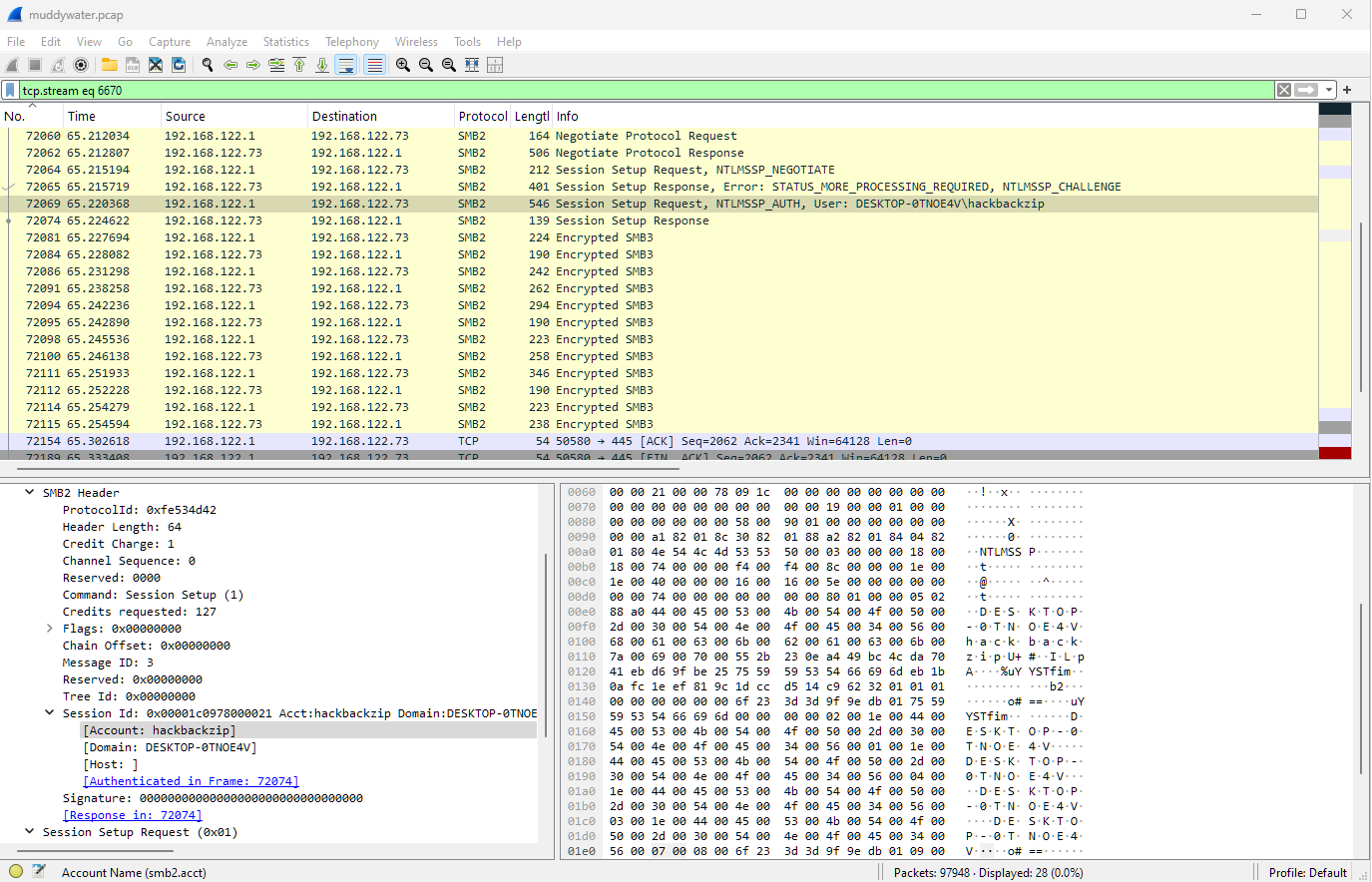
This updates the display filter to tcp.stream eq 6670 where we can see an Encrypted SMB3 conversation, and the username DESKTOP-0TNOE4V\hackbackzip: